- Industries
Industries
- Functions
Functions
- Insights
Insights
- Careers
Careers
- About Us
- Technology
- By Omega Team

Biometrics are unique physical or behavioral human characteristics that are used to digitally identify an individual by measurement and statistical analysis of people’s unique physical and behavioral characteristics to give access to systems, devices, or data. The basic principle of biometric authentication is that every individual can be correctly recognized by their intrinsic physical or behavioral characteristics.
Fingerprints, facial patterns, voice, and typing cadence are examples of biometric identifiers. Each of these identifiers is regarded as unique to the individual, and they can be used in conjunction to improve identification accuracy.
Biometric systems, also known as Identity Verification (IV) systems, are the art of developing authentication procedures that use biometric characteristics to automatically identify, measure, and validate a live human. The biometric system is based on the idea that each individual is unique in terms of physical and behavioral characteristics. Biometric identifiers are permanent, unique, and distinct from one another. The objective of building such systems is to improve the digital world’s safety and security. Biometric recognition systems are in high demand for preserving user authentication and identity in forensics, defense, surveillance, personal identity, and banking. It is difficult for an imposter to recognize and fake a registered person’s biometric modality, which contributes to the growth and popularity of biometric systems. The key features that separate conventional security techniques are their resilience, high accuracy rates, and difficulty in spoofing.
Types of Biometrics
Biometric identification is associated with inherent human traits. They are classified into two types: physical identifiers and behavioral identifiers. Physical IDs, for the most part, are immutable and device agnostic:
Fingerprint Recognition: The use of ridges and valleys on the surface tips of a human finger to identify a person. Fingerprint scanners have grown widely in recent years as a result of their extensive use of smartphones. Any item that can be touched, such as a phone screen, a computer mouse or touchpad, or a door panel, has the potential to transform into a simple and convenient fingerprint scanner.
Physiological recognition: The 2nd most common method of authentication is facial recognition, by analyzing the facial characteristics or patterns to authenticate or recognize an individual’s identity. The majority of face recognition systems employ either eigenfaces or local feature analysis. Hand geometry recognition, geometric features of the hand such as the lengths of fingers, and the hand’s width to identify an individual. IRIS or retinal scanning, palm vein recognition, and ear recognition are further image-based verification methods.
Voice recognition: The use of a speaker’s voice to determine his or her identity for access control purposes. If the speaker claims to be of a particular identity and the voice is utilized to validate that assertion. A 1:1 match occurs when one speaker’s voice is matched to one template (also known as a “voiceprint” or “voice model”). Speaker verification is commonly used as a “gatekeeper” to enable access to a secure system (ex. telephone banking). These systems function with the user’s awareness and, in most cases, with their participation.
Signature recognition: The authentication of a person by the examination of handwriting style, particularly the signature. Static and Dynamic digital handwritten signature authentication are the two main forms. Static is often a visual comparison of one scanned signature to another scanned signature or a scanned signature to an ink signature. It is possible to use advanced algorithms to compare two scanned signatures. Dynamic is becoming increasingly common as ceremony data, as well as the signor’s A, B, C, and D coordinates, are recorded from the signing device. Digital signature scanners are already widely used at retail checkouts and in banks, and therefore are an excellent choice for circumstances where users and customers are already familiar with signing their names.
DNA recognition: Identifying an individual using the analysis of segments from DNA. DNA sequencing scanners take too long to process the data. But this is beginning to change with the latest technological developments. A $1,000 scanner that can perform a DNA match within a few minutes and prices are expected to continue to fall.
Typing patterns recognition: Use of the unique characteristics of an individual typing for establishing identity. Everyone has a unique typing style. The rate at which they type, the time it takes to move from one letter to the next, and the degree of impact on the keyboard.
Physical or Gait movements recognition: Use of an individual walking style to determine identity. The way a person walks is unique to them and may be used to authenticate individuals in a facility or as a secondary layer of authentication in, particularly sensitive areas.
Biometrics Adoption
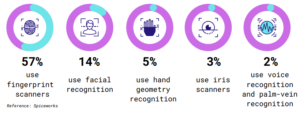
A total of 492 people from North America and Europe took part in the Spiceworks poll, which was conducted in February 2018. Respondents are among Spiceworks’ millions of IT professionals, and they represent a wide range of organization sizes, including small, medium, and large firms. Manufacturing, healthcare, nonprofits, education, and government are among the industries represented among the respondents.
Figure 1: Breakdown of Companies using Biometric Authentication
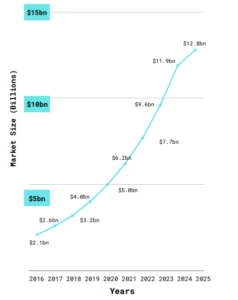
Global Healthcare Biometrics Market
The global healthcare biometrics market size was valued at USD 5 billion in 2020 and is expected to witness a CAGR of 24.2% over the forecast period of 2021 to 2025. Rising healthcare IT applications along with increasing awareness and need for cybersecurity and biometric development catering to healthcare facilities are the key driving factors attributed to the market’s rise.
Figure 2: Global Healthcare Biometrics Market Size
Attacks and Threats to Biometric Data
Biometric systems offer many benefits over traditional methods such as identification cards and passwords, there are a variety of assaults against biometric data. Direct and indirect assaults on biometric systems are examples of biometric system assaults. Direct cyberattacks are attacks on the system without knowledge of the system’s functioning, feature extraction methods, and matching algorithms employed. Sensor attacks are another name for direct attacks. Indirect attacks on biometric systems need knowledge of the system’s inner workings, such as an attack on the feature extraction module, an attack on the communication system, an attack on the matching module, and so on.
These are some of the biometric malicious attacks:
Fake Biometric: An attacker uses fake biometric samples to get access to the system. The lens on an iris, Fake face masks, fake silicon fingerprint, etc is few such malicious attacks on the sensor.
Spoofing the Feature set: The attacker changes the feature set to a fake one. To gain confidential information, attackers attack various networks and spread malware.
Replay Attack: The attacker injects the data stream of the biometric system between the sensor and the processing system. A replay attack is a multistep attack. It first intercepts or copies the sensor transmission, then alters the information, thus finally replaying the data.
Trojan horse attack: The feature extractor is replaced to produce the desired features and to add them to the existing database.
Securing Biometric Systems
To get protected from such attacks we need some security functionalities for the biometric. The security requirements of biometrics are authenticity, integrity, non-repudiation, confidentiality, and availability.
Authenticity: In biometric authenticity, two types are there, data origin authenticity and entity authenticity. Data origin authenticity ensures the genuineness and originality of the information. Whereas the entity authenticity confirms that all entities involved in the overall processing are the ones that they claim to be.
Integrity: The integrity of the authentication process is dependent on the integrity of the biometric reference. To ensure the integrity of the biometric, we make sure to have trustworthy biometric references.
Non-repudiation: It forbids a recipient of biometric data from denying having sent or received biometric information.
Confidentiality: Access control mechanisms and various forms of encryption techniques provide the confidentiality of stored and transmitted biometric data.
Availability: The availability of biometric services is ensured through redundancy in equipment and component levels.
Benefits of Biometrics in the Healthcare Industry
Optimizing Time: This is one of the most important advantages of using biometrics as an authentication technique. Instead of filling out forms and showing identification at the different verification points. Ex. A patient just has to place their finger on a reader, which solves the complete procedure of their access to services.
Improving Quality: With biometric identification, it is now feasible to integrate clinical data by reducing medical record duplication. It also increases clinical record accuracy while also enhancing the quality of the health information system and, most importantly, eliminates inappropriate treatments. All of this, in turn, contributes significantly to improved healthcare delivery and quality.
Cost optimization: The use of biometrics and changes in identification processes, both for patients and employees, are showing the first signs of a decrease in healthcare expenditures. The expense of maintaining the previous and inefficient approach for accurately identifying patients is eliminated since a biometric system does not incur maintenance costs owing to credential loss and forgetting. This new method generates less physical documentation (paperless), and document management can be improved. As a result, it significantly lowers health fraud and its associated expenses.
Conclusion
The world of technology needs security, Biometrics help in stepping up towards the secured systems. Biometrics is getting adapted by all the sectors. The healthcare sector is growing rapidly with an expected CAGR of 22.4% year on year. As the healthcare industry evolves, it is only natural to expect the incorporation of more biometric data, especially given that face recognition is becoming a significant modality on consumer devices. Biometrics contributes to making systems more secure. To assure the security of biometric data, getting awareness about the attacks and working on the solutions seem very important. Biometric technology is cost and time-effective. The use of it offers greater security and convenience than traditional methods of personal identification.
Subscribe
Select topics and stay current with our latest insights
- Functions