- Industries
Industries
- Functions
Functions
- Insights
Insights
- Careers
Careers
- About Us
- Technology
- By Omega Team

Cloud computing provides computing needs or computing services including servers, networking, storage, applications, intelligence, and analytics over the internet to provide innovation, versatile capital and economies of scale. You usually only pay for the cloud services that you use, helping to reduce your operating costs, operate your infrastructure more effectively and scale up as your business needs shift. (Microsoft Azure, n.d.) Cloud computing can be looked like an ever-evolving paradigm.
The NIST definition of cloud computing is as follows: Cloud computing is a model for allowing universal, easy, on-demand network access to a common pool of configurable computing resources (e.g., networks, servers, storage, software, and services) that can be easily distributed and released with minimal management effort or interference between service providers. This cloud model consists of five core elements, three service models, and four implementation models.
Essential Attributes
- On-demand self-service: A customer can have computing capabilities unilaterally, such as server time and network storage automatically without requiring human intervention with any service provider, as necessary.
- Broad network access: Over the network, capabilities are available and accessed via standard mechanisms that promote the use of heterogeneous thin or thick client platforms (example: tablets, laptops, mobiles, workstations, etc.)
- Resource pooling: The computing resources of the company are pooled to support multiple customers using a multi-tenant model, with dynamically allocated and reassigned different physical and virtual resources according to customer demand. There is a sense of location freedom in that the consumer usually does not have power or information over the exact position of the services offered but may be able to determine the position at a higher level of abstraction.
- Rapid Elasticity: Capabilities can be provided and released elastically, in some cases automatically, to swiftly scale outward and inward commensurate with demand. For the user, the provisioning capacities always seem infinite and can be allocated in any quantity at any time.
- Measured Service: Cloud systems automatically monitor and optimize resource usage by using a metering capability1 at some level of abstraction relevant to the form of service (e.g., storage, processing, bandwidth, and active user accounts). The use of services can be tracked, managed and recorded, thus ensuring accountability for both the provider and the user of the service used.
Service Model
Any technology or application of technology should have flexible service models for practical applications so that the end-user has a choice, which would suit his requirements. Similarly, for cloud computing, there are three service models that the client can leverage according to his business need.
- Software as a service (SaaS): The capacity offered to the user is to use the applications running on a cloud platform of the provider. The applications can be accessed from different client devices through either a thin client interface, such as a web browser (e.g. web-based email), or a software interface. The customer does not monitor or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even the functionality of individual applications, with the possible exception of user-specific configuration settings. Examples: Google Apps (Gmail, Docs), Salesforce.com.
- Platform as a service (PaaS): The power given to the user is to deploy customer-created or acquired applications on the cloud infrastructure generated using the provider supported programming languages, databases, services, and software. The user does not manage or monitor the underlying cloud infrastructure like network, servers, operating systems, or storage, but has monitored over the applications deployed and probably the application-hosting environment configuration settings. Examples: Programming API, Google App-Engine, Windows Azure.
- Infrastructure as a service (IaaS): The consumer’s capacity is to include computation, storage, networks, and other fundamental computing tools where the user can install and run arbitrary software that can include operating systems and applications. The user does not operate or monitor the underlying cloud infrastructure, but has control over operating systems, storage, and deployed applications; and probably restricted control over select networking components (e.g., host firewalls). (Mell & Grance, 2011). Examples: Amazon (EC2, S3), VM Management.
- Public Cloud: The cloud infrastructure is being given to the public for free use. It may be owned, managed, and controlled by, or some combination of, a corporation, academic, or government agency. It resides at cloud provider premises.
- Hybrid Cloud: The cloud infrastructure is composed of two or more different cloud infrastructures (private, group, or public) that remain unique entities but are connected together through standardized or proprietary technology that allows portability of data and applications (e.g. cloud bursting for cloud load balance).
Global Market Research
Using cloud storage technology not only provides cost savings but also makes software available at any time and from any place to all users on the network. In 2012, the global storage industry reported revenues of $9.12 billion with a growth rate of 16.7 percent compared to 2011 revenues. The big driver of the global demand for cloud computing services is their cost-effective offerings. The global cloud computing market is expected to expand strongly with a 6.5% CAGR in the period 2019-2024.
Cloud computing was listed in 71 of 77 Gartner’s hype cycles for 2011 with 3 of them dedicated to different aspects of cloud computing in varying degrees. Public cloud will make up two-thirds of the size of the sector by 2020, i.e. USD 159.3 billion.
Figure 1: World Wide Public Cloud Service Revenue Forecast, 2018-2022
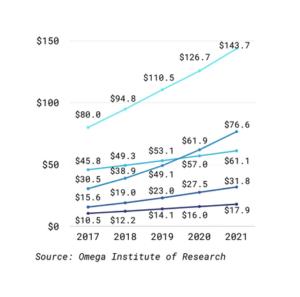
Estimation made by Gartner is that the worldwide public cloud computing market will rise from $182.4B in 2018 to $331.2B in 2022, hitting a compound annual growth rate (CAGR) of 12.6%. Infrastructure as a Service (IaaS) spending is expected to rise from $30.5B in 2018 to $38.9B in 2019, up 27.5% a year. Platform as a Service (PaaS) spending is expected to rise from $15.6B in 2018 to $19B in 2019, up 21.8% in one year.
Market Intelligence, Supply Chain Management, Project and Portfolio Management, and Enterprise Resource Planning (ERP) will see the highest increase in end-user spending on SaaS applications through 2022. Gartner estimates that the global demand for public cloud services will rise from $182.4B in 2018 to $214.3B in 2019, a 17.5% increase in just one year. By the end of 2019, more than 30% of new computing expenditures by technology providers will move from cloud-first to cloud-only, further reducing licensing computing spending and rising subscription-based cloud revenue.
Figure 2: CAGRs of Worldwide Public Cloud Service Revenue Split
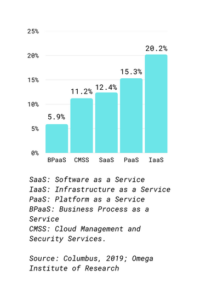
Key players in this competitive landscape: Microsoft, Amazon, IBM, Google, Oracle, Alibaba, NTT Data, Salesforce, Baidu, others.
This allows customers to understand which Ikea furniture fits in their room according to specific dimensions, as well as getting a visual understanding of what their room would look like using specific items. Customers can rearrange and select/drop items from Ikea’s vast catalog creating the opportunity for limitless variation.
Figure 3: All Cloud Services Market Share, 2019
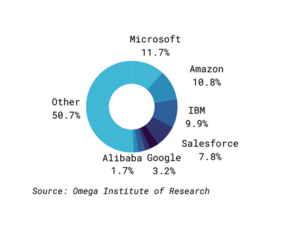
Cloud Security
Cloud security refers to the methods and techniques used to protect cloud computing infrastructures from both external and internal cyberattacks. Cloud computing, or the transmission of information technology services via the internet, has become a necessity for organizations and governments looking to boost innovation and cooperation. To keep data and applications in the cloud safe from current and upcoming cybersecurity threats, cloud security, and security management best practices aimed to prevent unauthorized access are required.
Cloud Security Responsibilities
Most cloud companies strive to provide consumers with a secure cloud. Preventing breaches and maintaining public and customer trust is central to their business model. Cloud providers can try to avoid cloud security vulnerabilities with their services, but they have no control over how customers use them, what data they add, or who has access. Customers’ configuration, sensitive data, and access policies can all compromise cloud security. The cloud provider and the cloud consumer share different levels of security responsibility in each public cloud service type. These are the different types of services:
Software-as-a-service (SaaS) — Customers are responsible for securing their data and user access.
Platform-as-a-service (PaaS) — Customers are responsible for securing their data, user access, and applications.
Infrastructure-as-a-service (IaaS) — Customers are responsible for securing their data, user access, applications, operating systems, and virtual network traffic.
Customers are responsible for securing their data and managing who has access to it in all sorts of public cloud services. Cloud computing data security is critical to properly embracing and reaping the benefits of cloud computing. Organizations contemplating popular SaaS products such as Microsoft Office 365 or Salesforce should evaluate how they will meet their shared duty for cloud data security. Those contemplating IaaS services like Amazon Web Services (AWS) or Microsoft Azure should develop a more comprehensive strategy that begins with data and extends to cloud app security, operating systems, and virtual network traffic— all of which might create security risks.
Latest Trends in Cloud Computing
Dev Ops
The phrase DevOps combines two terms: development and operations. It has resulted in Continuous Delivery, Integration, and Deployment, minimizing the gap between the development and operations teams. Heavy applications and software require complicated and complex tech stacks that require a lot of time and effort to design and configure, which cloud computing can readily alleviate. It provides a wide range of tools and technologies for quickly developing, testing, and deploying applications. They can be tailored to meet the needs of the client and discarded when no longer in use, making the process for development teams more streamlined and cost-effective.
Cloud Cryptography
Data stored in the cloud must be protected and secured against external assaults and intrusions. To do this, cloud cryptography is a frequently used technology for securing data in the cloud. Because all data is secured using either encryption techniques or the concept of the private key, it allows users and customers to use shared cloud services easily and reliably. It has the potential to render plain text illegible and restrict the view of the data being conveyed. The best cloud cryptographic security techniques are those that don’t slow down data flow and provide security without delaying sensitive data sharing.
Mobile Cloud Computing
It combines cloud computing, mobile computing, and wireless networks to give mobile consumers, network operators, and cloud computing specialists services such as seamless and abundant computational resources. The console is the handheld device, and all processing and data storage occurs outside of the physical mobile device. Mobile cloud computing has several
advantages, including no need for expensive hardware, longer battery life, increased data storage capacity and processing power, improved data synchronization, and high availability owing to “store in one place, accessible from everywhere.” The backend handles the integration and security elements, allowing for a wide range of access ways to be supported.Green Cloud Computing
The use of energy-efficient and hence produce economically friendly cloud computing systems is a big challenge in the cloud. Data centers, which contain a huge number of computers, cables, air conditioners, networks, and other components, consume a lot of energy and emit a lot of carbon dioxide into the atmosphere. Green Cloud Computing aims to make virtual data centers and servers more energy-efficient and ecologically friendly. Cloud resources frequently consume a lot of electricity and energy, resulting in a power shortage and harming the global climate. Green cloud computing offers ways to make these resources more energy efficient while also lowering operating expenses. This focuses on energy management, server and data center virtualization, e-waste recycling, and environmental sustainability.
Edge Computing
It is a more advanced and efficient type of Cloud computing based on the principle of processing data closer to the source. Edge Computing refers to the fact that all processing will take place at the network’s edge, rather than on a centrally managed platform or in data warehouses. Different data processing techniques and mechanisms are distributed across different positions in edge computing. This allows data to be delivered to the nearest node and processing to take place at the edge. Because the data is closer to the source, it is also more secure, and it decreases late reaction time and latency without compromising productivity.
Containerization
In cloud computing, containerization is a method for virtualizing operating systems. Remote resource procedures enable the user to deal with a program and its dependencies. In cloud computing, containers are used to build pieces that help with operational efficiency, version control, developer productivity, and environmental stability. The infrastructure has been improved since it allows for more detailed control over resource activities. Containers in online services help with data security, elasticity, and availability in cloud computing environments. Containers have several benefits, including a consistent runtime environment and the ability to reuse resources. Containers provide several advantages over virtual machines, including a consistent runtime environment, the flexibility to run practically anywhere, and reduced overhead.
Subscribe
Select topics and stay current with our latest insights
- Functions