- Industries
Industries
- Functions
Functions
- Insights
Insights
- Careers
Careers
- About Us
- Technology
- By Omega Team

Cybercrime is defined as any type of criminal or illegal activity that is perpetuated in a virtual environment, so it always involves devices — such as computers — and their data, systems, and networks. They happen in a distinctive social environment: the “cyberspace”, rather than the terrestrial “real” space.
The most common cybercrimes are hijacking websites, sabotage, damaging and disabling devices, spying and harassment, destruction, theft and sharing of private information, distributed denial of service (DDoS) to make resources unavailable, phishing to obtain sensible data, malware spreading to intentionally cause damage, among others.
As technology has immensely evolved in the last decades so have the forms, the volume, and the fast pace of digital criminal activity. Since the late 1980s, when computers and the internet started to become mainstream we have learned about computer viruses, worms, and hackers. However more recently we are starting to understand the extent to which cyber-crimes can have an impact on enterprises and public safety alike. In 2013 three billion Yahoo accounts were breached and their information was stolen. In 2018 the data of 500 million guests of the Marriot, the world’s largest hotel chain, was compromised.
Cybercrime causes significant damage, sensitive data is stolen and organizations lose billions of dollars and their reputation. With the COVID-19 crisis, there has been a spike in cybercriminal activities and for 2021 it is expected that the losses will amount to 6 trillion dollars (Morgan, 2020).
Virtual criminals seek to profit through ransom, fraud, or money laundering, to spread sensible information and materials, and to attack supply chains. Over the years they have established their own ecosystem, with an underground economy, many highly qualified criminal groups, and in connection to global politics.
Criminologists and lawmakers are continuously debating as technologies progress on how to conduct prevention and control of cybercrimes. Unfortunately not every nation has a deep understanding or efficient management against them, laws fall behind new technologies, typifications vary among countries and this lack of common standards and the fragmentation of production make the defense and prosecution of attacks much harder. It has become crucial to share threat information and best practices for security between private and public organizations across the globe.
The rise of the Internet of Things (IoT) and the digital transformation of essential, social, and economic activities worldwide — from shopping to health services and even voting — demand that we stay up to date with cybersecurity technologies and strategies. It has become a must for every type of organization to think about these issues, not only companies that provide IT services.
Cybersecurity Tendencies & Supporting Evidence
Cybersecurity consists of the engineering of software, techniques, mechanisms, and rules that control how information that is stored in a device is used and accessed and who can do it, so it can protect a digital system and its network against criminal activity. The objective of cybersecurity is to resist and monitor what happens when there is an attack and to respond with speed, but fundamentally to guarantee protection by design. The pillars of cybersecurity are confidentiality, availability, and integrity of data, functions, and services.
The benefits of implementing safety strategies and technologies can be seen for example in the Accenture 2020 State of Cybersecurity report, which compared the cyber resilience between organizations that are investing more in scale, training, and collaboration and those that are approaching cybersecurity in a more conservative way.
Figure 1: Investments in Organizations in Cybersecurity
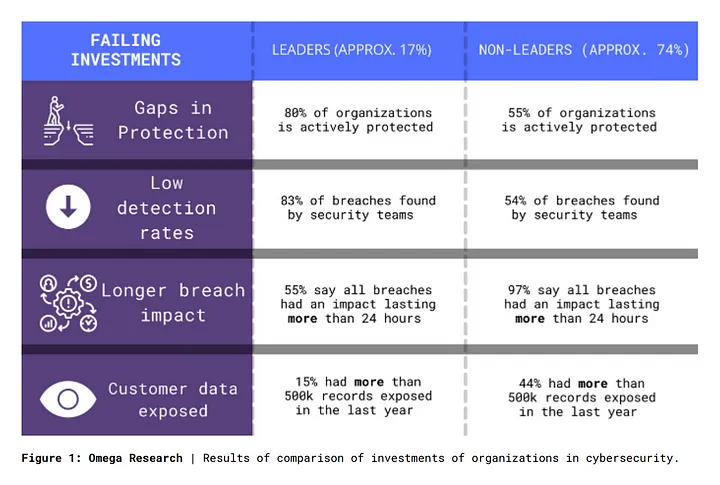
The differences amongst leader and non-leader organizations are noticeable in all studied aspects: they are securing 25% more of their organization, finding 29% more breaches, being 42% more time effective, and have 29% less exposed consumer data.Another comprehensive study was carried out by Comparitech among 75 countries to measure which ones are the most cyber-safe, comparing the amounts of different types of attacks they have endured to their Global Cybersecurity index, which in turn is measured according to their legal, technical, organizational, R&D and cooperation in cybersecurity.
Figure 2: Worldwide Cybercrime Statistics
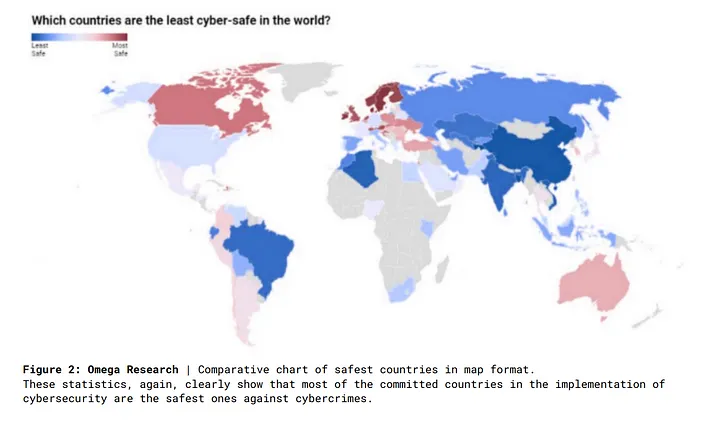
Between the years 2000 and today, several security mechanisms have been developed and have continued to evolve in accordance with new technologies and threats. Most of these are now standards for safety policy recommendations worldwide.
The most used are:
1. Fire-walling to monitor, block or allow traffic from authorized and safe servers.
2. Antivirus software, scanners, and management servers with continuously updated signatures for viruses, spyware, and malware.
3. Two-way or two-factor authentication, with tokens in multiple devices that provide encrypted access keys.
4. Proxy servers that function as intermediaries or gateways between devices.
5. Standardization of end-to-end communication encryption through SSL and TLS protocols and certificates in browsers.
6. Virtual Private Networks (VPN) to encrypt access sessions.
7. Network intrusion detection systems (IDS) and host intrusion detection systems (HIDS) to listen and monitor network and internal traffic.
8. Security information management servers (SIM) for activity logging with Network Behavioral Analysis and comparison to vulnerabilities databases.
9. Encryption and authentication embedded in hardware.
10. Enterprise sandboxes to preemptively detect threats across organizations.
All these technologies are constantly evolving on par with new developments. For instance, in the last couple of years, there is an emerging cryptography a technology called homomorphic encryption which is a mathematical method to share data without actually sharing it.
Conclusions
The digital is here to stay, even more so now after the COVID-19 crisis. Every day more aspects of our lives and organizations are adopting a virtual existence. In order to ensure the safety of our data, networks, and cyber experiences it is important to understand the risks of cybercrime and the benefits of the use of security technologies and strategies. Cybersecurity is a shared challenge and responsibility between companies, institutions, governments, and users alike.Many organizations around the world, especially in the last 10 years, are starting to be proactive, integrating Chief Security Officers (CSOs) into their boards, trying to make their systems secure by design, and understanding that it needs to be part of their everyday culture. However many others are still not investing or thinking enough about these issues. New complex technologies are being introduced and implemented such as cloud computing, blockchain, AI, 5G networks, quantum computing, that will definitely bring great new benefits but they can also be considered as great new emerging dangers.
It is a fact that cyber-attacks will continue to happen. Fortunately, the numbers are showing that the more investment and education in cybersecurity the safer our countries, organizations, and user experiences will be.
Subscribe
Select topics and stay current with our latest insights
- Functions