- Industries
Industries
- Functions
Functions
- Insights
Insights
- Careers
Careers
- About Us
- Technology
- By Omega Team
As cyber threats grow in sophistication, traditional security models relying on perimeter defenses have proven insufficient. Enter Zero Trust: a cybersecurity framework that operates under the principle of “never trust, always verify.” Instead of assuming trust based on location or credentials, Zero Trust requires continuous authentication and validation of users, devices, and network activity. This approach is reshaping how businesses secure their digital assets in an increasingly interconnected world. By enforcing strict access controls and leveraging AI-driven threat detection, Zero Trust minimizes attack surfaces and mitigates risks in real time. Organizations adopting this model gain enhanced visibility, ensuring that security policies adapt dynamically to evolving threats. As remote work and cloud adoption expand, Zero Trust becomes a critical strategy for safeguarding sensitive information. Businesses that prioritize Zero Trust today will be better positioned to navigate the challenges of tomorrow’s cybersecurity landscape.
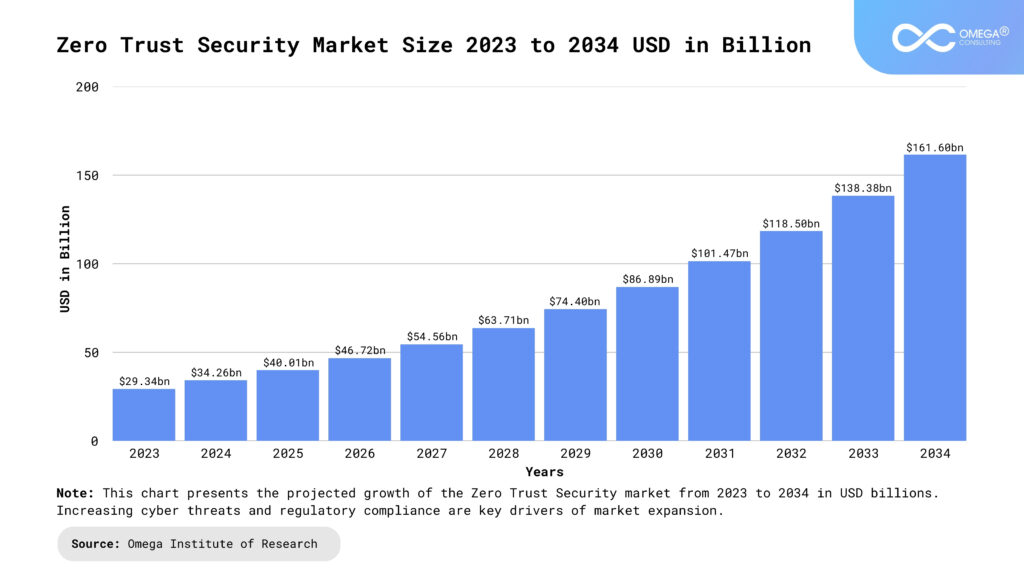
This chart presents the projected growth of the Zero Trust Security market from 2023 to 2034 in USD billions. Increasing cyber threats and regulatory compliance are key drivers of market expansion. Core Principles of Zero Trust
Zero Trust enhances security by eliminating implicit trust and enforcing strict access controls. It replaces perimeter-based defenses with continuous verification and proactive threat detection. This approach minimizes vulnerabilities, mitigates breaches, and strengthens cybersecurity resilience.
Verify Explicitly: Authentication and authorization must be continuously validated to ensure only legitimate users and devices gain access. This process involves multiple factors, including user identity, device security posture, location, and real-time risk assessments. Unlike traditional security models, Zero Trust does not assume that users inside the network are inherently safe. Continuous verification ensures that access decisions are dynamic and based on real-time security conditions.
Least Privilege Access: Users and applications should be granted only the minimum level of access required to perform their specific roles. This principle reduces the risk of attackers exploiting excessive permissions to move laterally within the system. By implementing role-based access control (RBAC) and just-in-time (JIT) access policies, organizations can limit exposure to sensitive data and minimize potential damage. Enforcing the least privilege model strengthens security by restricting unauthorized access and reducing insider threats.
Assume Breach Mentality: Organizations should operate under the assumption that internal networks are already compromised. Instead of reacting to security incidents after they occur, Zero Trust enforces proactive measures such as segmentation, continuous monitoring, and automated threat detection. This approach ensures that even if an attacker gains access, their ability to move laterally or escalate privileges is severely restricted. By treating every request and interaction as potentially malicious, organizations can significantly reduce the impact of breaches.
Micro-Segmentation: Networks are divided into small, controlled segments to limit lateral movement in case of a breach. By isolating workloads, applications, and devices, organizations can prevent attackers from easily navigating through the network. This strategy ensures that a compromised system does not lead to widespread damage by containing threats within isolated zones. Micro-segmentation enhances overall security by enforcing strict access policies between network segments.
Continuous Monitoring and Analytics: Security teams leverage AI-driven insights, behavioral analytics, and automated responses to detect anomalies and prevent threats in real time. By continuously analyzing access patterns and system behavior, organizations can identify suspicious activities before they escalate into full-scale breaches. Automated threat detection mechanisms provide rapid responses to mitigate risks and enhance incident response capabilities. This continuous monitoring approach ensures that security teams maintain visibility and control over their digital environments.
Industries Adopting Zero Trust
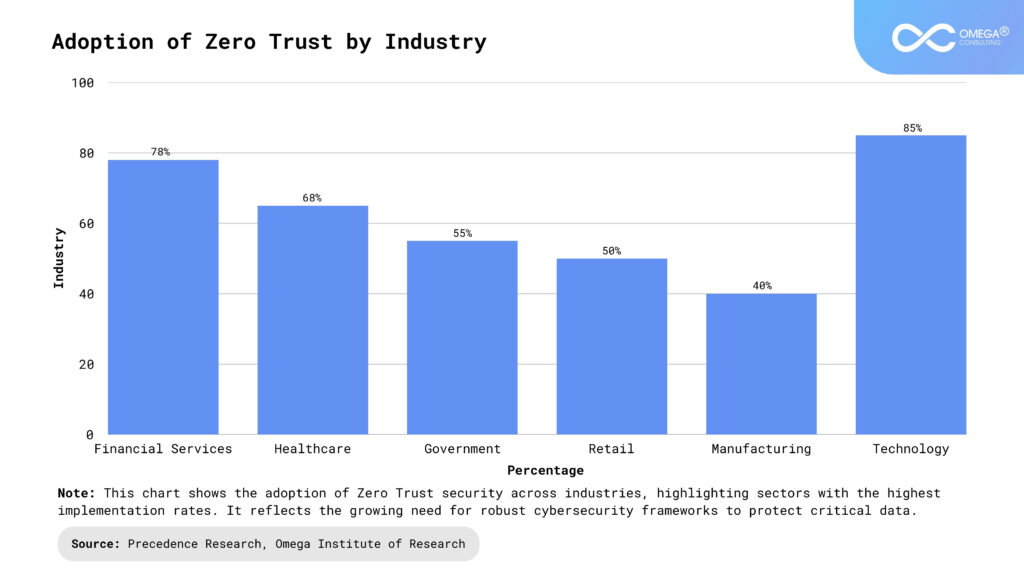
Various industries are adopting Zero Trust to enhance security, protect data, and meet regulations. As cyber threats grow, sectors like finance, healthcare, government, and technology use Zero Trust to secure remote work, cloud systems, and critical assets. This approach minimizes risks and strengthens cybersecurity resilience.
Financial Services: Financial institutions face stringent regulatory requirements and significant cyber threats due to the high value of financial data. Zero Trust helps banks, insurance companies, and fintech firms protect sensitive customer information, prevent fraud, and maintain compliance with regulations like GDPR, PCI-DSS, and SOX. By enforcing strict identity verification, continuous monitoring, and least-privilege access, financial organizations can reduce the risk of data breaches. As cybercriminals employ more sophisticated attack methods, Zero Trust provides an essential defense against financial fraud and cyber intrusions.
Healthcare: Hospitals and healthcare providers implement Zero Trust to safeguard patient data, prevent ransomware attacks, and ensure compliance with HIPAA and other privacy regulations. The growing adoption of telemedicine, IoT-enabled medical devices, and cloud-based health records has increased the need for robust security measures. Zero Trust protects healthcare networks by continuously verifying access requests and restricting lateral movement within systems. By preventing unauthorized access to electronic health records (EHRs) and medical devices, Zero Trust helps maintain patient privacy and healthcare system integrity.
Government and Defense: Government agencies, including defense and intelligence sectors, have mandated Zero Trust architectures to protect national security from cyber threats and espionage. The U.S. government’s executive order on cybersecurity underscores the importance of Zero Trust in securing critical infrastructure and classified data. By implementing continuous authentication, network segmentation, and real-time threat detection, Zero Trust helps prevent state-sponsored attacks and insider threats. As cyber warfare tactics evolve, Zero Trust remains a foundational security strategy for protecting sensitive government systems.
Technology and SaaS Companies: With the rise of remote work, cloud computing, and global software development teams, technology and SaaS firms rely on Zero Trust to secure intellectual property, customer data, and development pipelines. Zero Trust ensures that employees, contractors, and third-party vendors access only the resources necessary for their roles, reducing the risk of data leaks and insider threats. By enforcing strict access controls and continuously monitoring cloud environments, technology companies can prevent unauthorized access and enhance overall security. This approach is particularly crucial in protecting software supply chains and DevOps environments.
Manufacturing and Critical Infrastructure: Energy companies, utilities, and industrial manufacturers integrate Zero Trust to protect operational technology (OT) systems from cyber threats that could disrupt supply chains and essential services. As industrial control systems (ICS) and Internet of Things (IoT) devices become increasingly connected, securing these systems from cyberattacks is a top priority. Zero Trust prevents unauthorized access to critical infrastructure by enforcing strict access policies, monitoring network traffic, and segmenting systems to contain potential threats. By adopting this security model, manufacturing and critical infrastructure sectors can mitigate risks and ensure business continuity.
Should Your Company Adopt Zero Trust?
The increasing frequency of cyberattacks, data breaches, and insider threats make Zero Trust a compelling choice for businesses of all sizes. Here’s why companies should consider adopting this model:
Enhanced Security Posture: Zero Trust strengthens cybersecurity by minimizing attack surfaces and restricting access to only what is necessary. By enforcing least-privilege access, organizations limit potential entry points for attackers. Continuous authentication and network segmentation further reduce the risk of unauthorized access. This proactive approach helps protect sensitive systems and data from evolving cyber threats.
Cloud and Remote Work Protection: As hybrid work environments grow, securing cloud applications and remote access is critical. Zero Trust ensures that users, regardless of location, authenticate before accessing corporate resources. Strong identity verification and endpoint security measures prevent unauthorized access. This model provides secure, seamless connectivity for remote employees while protecting sensitive data.
Regulatory Compliance: Many industries must adhere to strict identity verification and data protection regulations. Zero Trust inherently supports compliance with frameworks like GDPR, HIPAA, and PCI-DSS by enforcing strong access controls and continuous monitoring. Organizations can reduce legal risks and avoid penalties by maintaining strict security standards. Implementing Zero Trust ensures ongoing adherence to regulatory requirements.
Proactive Threat Mitigation: AI-driven monitoring in Zero Trust detects anomalies and potential threats in real time. Automated threat responses help prevent security incidents before they escalate. By continuously analyzing user behavior and network traffic, organizations can identify and block suspicious activity. This proactive approach reduces the risk of undetected breaches and enhances overall cybersecurity resilience.
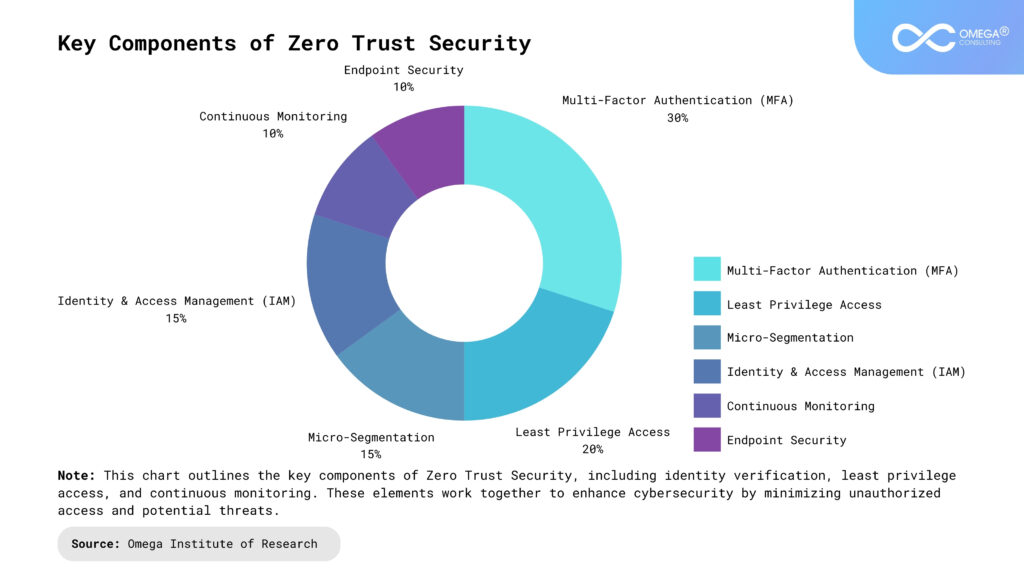
Key Components of Zero Trust Implementation
Identity and Access Management (IAM): Strong authentication mechanisms, such as multi-factor authentication (MFA) and role-based access control (RBAC), ensure that only authorized users gain access. IAM verifies user identities before granting permissions, reducing the risk of unauthorized access. By continuously validating credentials, organizations prevent credential-based attacks. This approach strengthens security by enforcing strict access policies.
Network Segmentation and Micro-Segmentation: Organizations should divide their networks into smaller, controlled zones to limit lateral movement in case of a breach. By segmenting critical assets, Zero Trust prevents attackers from accessing the entire network if they infiltrate one section. This reduces the blast radius of cyber incidents and enhances containment. Enforcing strict access rules between segments helps maintain security integrity.
Endpoint Security: Devices accessing corporate networks must comply with security policies to minimize risks. Endpoint detection and response (EDR) solutions and device posture assessments help identify and mitigate potential threats. Ensuring that only secure, compliant devices connect to the network reduces the likelihood of malware infections. Continuous monitoring of endpoints prevents unauthorized access and data breaches.
Zero Trust Network Access (ZTNA): ZTNA replaces traditional VPNs by enforcing strict authentication and access controls at the application level. Instead of granting network-wide access, users are verified continuously and only allowed access to specific applications. This approach reduces exposure to cyber threats and prevents unauthorized lateral movement. ZTNA enhances security for remote and hybrid work environments.
Security Monitoring and Analytics: Continuous monitoring with AI-powered threat detection helps organizations identify and respond to security incidents in real time. By analyzing user behavior and network activity, Zero Trust detects anomalies before they escalate into breaches. Automated responses and machine learning models strengthen cybersecurity resilience. This proactive approach ensures ongoing protection against evolving threats.
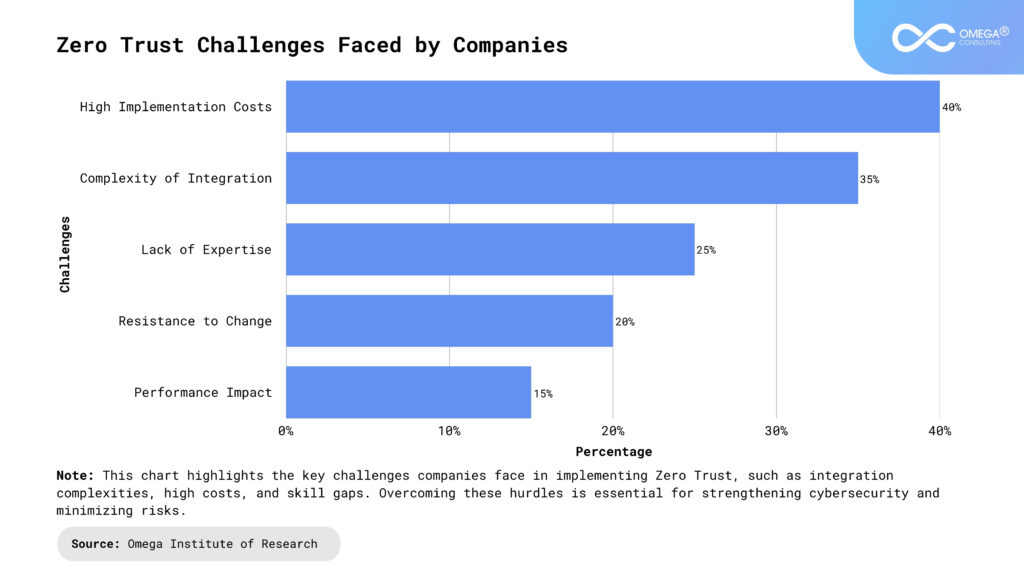
Challenges and Considerations
Despite its benefits, implementing Zero Trust requires careful planning and investment. Some common challenges include:
Integration with Legacy Systems: Older infrastructure may not support modern authentication and access control methods, making Zero Trust implementation complex. Upgrading legacy systems or integrating them with Zero Trust solutions requires careful assessment and planning. Organizations may need additional security layers to compensate for outdated technologies. A phased approach can help minimize disruptions while enhancing security.
User Experience Concerns: Frequent authentication prompts and strict access controls can impact workflow efficiency. Striking a balance between security and usability is crucial to prevent employee frustration. Implementing adaptive authentication and single sign-on (SSO) can streamline access while maintaining security. User-friendly security measures encourage compliance and improve adoption rates.
Initial Costs: Implementing Zero Trust involves investments in identity management, network segmentation, and automation tools. While the upfront costs may be high, the long-term benefits outweigh the expenses by reducing security breaches and compliance risks. Organizations should prioritize key areas for phased implementation to manage costs effectively. A well-planned budget ensures sustainable Zero Trust adoption.
Change Management: Transitioning to Zero Trust requires educating employees and stakeholders about the new security model. Resistance to change can slow adoption, making training and communication essential. Organizations must foster a security-first culture to ensure compliance and smooth implementation. Engaging leadership and IT teams early helps drive successful Zero Trust adoption.
Future Trends in Zero Trust Security
AI and Machine Learning Integration: Artificial intelligence and machine learning will play a key role in Zero Trust by automating threat detection and response. Behavioral analytics will help identify anomalies and potential security risks in real time. These advancements will improve accuracy in access control decisions and reduce false positives. AI-driven security will enhance Zero Trust frameworks for proactive cyber defense.
Zero Trust for IoT and OT: As IoT and operational technology (OT) devices grow, Zero Trust will expand to secure these environments. Industrial control systems and smart devices require strict access controls to prevent cyber threats. Organizations will implement micro-segmentation and real-time monitoring to protect connected devices. Strengthening security in IoT and OT networks will be crucial for critical infrastructure resilience.
Cloud-Native Zero Trust: With businesses increasingly adopting multi-cloud environments, Zero Trust models will evolve to support cloud-native security. Dynamic access controls and continuous authentication will be essential for securing cloud workloads. Organizations will rely on identity-based security policies to protect distributed applications and data. Cloud-native Zero Trust will provide scalability and flexibility for modern IT infrastructures.
Zero Trust as a Service (ZTaaS): Managed security providers will offer Zero Trust as a service to help businesses streamline implementation. ZTaaS will provide pre-configured security frameworks, reducing complexity and cost for organizations. This approach will enable small and mid-sized enterprises to adopt Zero Trust without extensive in-house expertise. As demand grows, ZTaaS will become a key driver of Zero Trust adoption across industries.
Conclusion
Zero Trust is more than just a cybersecurity model—it’s a necessary evolution in protecting modern digital ecosystems. By shifting from implicit trust to continuous verification, organizations can secure critical data, streamline access, and minimize vulnerabilities without disrupting productivity. Implementing Zero Trust isn’t about adding complexity but about creating a security-first culture that adapts to emerging threats while supporting business agility. Companies that integrate intelligent authentication, real-time monitoring, and least-privilege principles will be better equipped to navigate today’s cyber risks. As digital transformation accelerates, Zero Trust provides the foundation for long-term resilience and trust. To strengthen your security posture and stay ahead of evolving threats, contact Omega today and discover how Zero Trust can redefine your organization’s defense strategy.
- https://www.cloudflare.com/learning/security/glossary/what-is-zero-trust/
- https://www.ibm.com/think/topics/zero-trust
- https://www.zscaler.com/resources/security-terms-glossary/what-is-zero-trust
- https://www.akamai.com/glossary/what-is-zero-trust
- https://www.techtarget.com/searchsecurity/definition/zero-trust-model-zero-trust-network
Subscribe
Select topics and stay current with our latest insights
- Functions